Backtrack 5 Website Hacking Pdf Book

Ethical hacking books PDF in 2017 – List of 2017 Hacking Readables. These books will provide you basics of security practices made in network to ensure that it is safe from the hackers. The language of these books & the method of explanation is that simple that any naive reader can learn from these. Top Hacking Books 2017 BackTrack 5. BackTrack 5 Wireless Penetration Testing Beginner’s Guide. Or just plain inquisitive about wireless security and hacking, then this book is for you. The book assumes that you have familiarity with Backtrack and basic wireless concepts. Kali Linux Wireless Penetration Testing Beginner’s Guide; Comment Cancel reply.
Boot iso from external hard disk download. Make External Hard Drive Bootable Windows 10 by AOMEI Partition Assistant. In the pop up window, the inserted USB will automatically be selected as the bootable device. What you need to do is to click “Browse” to select Windows 10 ISO. In the pop up window, the Win 10 ISO file will be listed. Oct 07, 2018 Mac OS X. Connect the external hard drive to your Mac OS X computer. Click on the Apple menu and select the option to restart your computer. Press and hold down the “Option” key immediately after you hear the startup chime. The boot selection menu will display on-screen. Click on the name of your external hard drive. At this moment your new external hard disk or flash drive is bootable but you need to execute one more command in order to transfer the files to your new drive. You have to type the following command line: xcopy f: *.* g: /e /f /h. Again replace the drive letters with the ones that apply to you.
Multiloader v5 67 executive branch branch. Archived from on 2009-02-09. 22 January 1998. Retrieved 2012-04-23. Archived from on 2007-04-01.
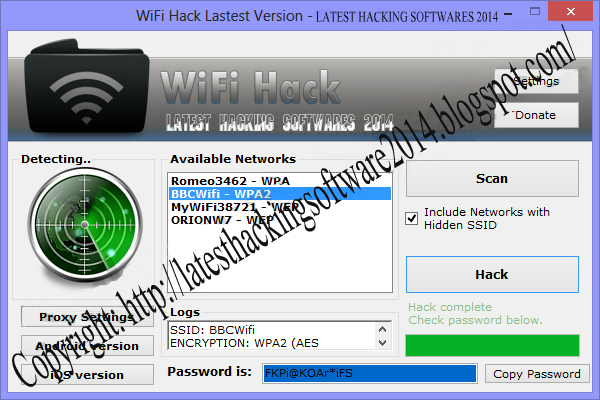
Backtrack 5 Website Hacking Pdf Books
Table of Contents
Hacking Tutorial Pdf
See more of Backtrack 5 r3 hacking tutorial pdf on Facebook. Create New Account. See more of Backtrack 5 r3 hacking tutorial pdf on Facebook. Forgot account? Create New Account. Backtrack 5 r3 hacking tutorial pdf. Business Service in Pakistan Employees Cooperative Housing Society, Sindh, Pakistan. Hack facebook with backtrack 5, tutorial, hacking facebook, how to hack facebook, hack facebook backtrack 5, SET Tutorial, hack facebook account, Backtrack. All Books Culture Health Humor Motivational Relationship. Walk The Wire by Vivek Ishwar. How to Hack Facebook Accounts with Backtrack 5. Hacky Shacky - Oct 2, 2014. Best Ethical Hacking Books PDF. 1) Hacking: The Art Of Exploitation (Second Edition) This post will be incomplete if we didn’t mention about this hacking book. This book is one of the best hacking books written by Jon Erickson, who is a computer security expert and has worked as vulnerability researcher and computer security specialist.
Backtrack 5 R3 Free Download
- 1 Introduction to Hacking
- Important Terminologies
- Categories of Penetration Test
- Types of Penetration Tests
- Understanding the Audience
- Structure of a Penetration Testing Report
- Vulnerability Assessment Summary
- Risk Assessment
- Methodology
- Detailed Findings
- 2 Linux Basics
- File Structure inside of Linux
- File Permission in Linux
- Linux Scheduler (Cron Job)
- Cron Permission
- Users inside of Linux
- What Is BackTrack?
- Changing the Default Screen Resolution
- Some Unforgettable Basics
- Getting to Know Your Network
- Services
- File Structure inside of Linux
- 3 Information Gathering Techniques
- Copying Websites Locally
- Yougetsignal.com
- TCP Traceroute
- UDP Traceroute
- Cheops-ng
- Intercepting a Response
- Netcraft
- Some Basic Parameters
- TIP regarding Filetype
- Xcode Exploit Scanner
- DIG
- Forward DNS Lookup with Fierce
- Reverse DNS Lookup with Fierce
- Automating Zone Transfers
- What Is DNS Cache Snooping?
- Automating DNS Cache Snooping Attacks
- SMTP Enumeration
- Bypassing CloudFlare Protection
- 4 Target Enumeration and Port Scanning Techniques
- Output
- 5 Vulnerability Assessment
- Testing SCADA Environments with Nmap
- Nessus Vulnerability Scanner
- Adding a User
- Nessus Control Panel
- Silent Dependencies
- Port Range
- Preferences
- Importing Nessus to Metasploit
- Resource
- 6 Network Sniffing
- Types of Sniffing
- ARP Attacks
- MAC Flooding
- Tools of the Trade
- Using ARP Spoof to Perform MITM Attacks
- Requirements
- Automating Man in the Middle Attacks
- DNS Spoofing
- 7 Remote Exploitation
- Understanding Network Protocols
- Server Protocols
- Binary Protocols
- Attacking Network Remote Services
- Overview of Brute Force Attacks
- Tools of the Trade
- Basic Syntax for Hydra
- Hydra GUI
- Cracking SSH with Medusa
- Cracking an RDP with Ncrack
- Combining Nmap and Ncrack for Optimal Results
- Attacking SQL Servers
- MSFConsole
- Useful Scans with Metasploit
- Nessus and Autopwn
- 8 Client Side Exploitation
- Client Side Exploitation Methods
- E-Mails with Malicious Attachments
- Introduction
- Creating a PDF Document with a Launch Action
- Tools of the Trade
- PDFINFO
- Attacking with PDF
- Social Engineering Toolkit
- Using Windows Box as Router (Port Forwarding)
- VPS/Dedicated Server
- Prerequisites
- Client Side Exploitation Methods
- 9 Postexploitation
- Acquiring Situation Awareness
- Enumerating with Meterpreter
- Privilege Escalation
- Escalating Privileges
- Backdoors
- MSFPayload/MSFEncode
- MSFVenom
- Dumping the Hashes
- References
- Cracking the Hashes
- John the Ripper
- Rainbow Crack
- Data Mining
- Identifying and Exploiting Further Targets
- psexec
- Acquiring Situation Awareness
- 10 Windows Exploit Development Basics
- Skeleton Exploit
- Figuring Out Bad Characters with Mona
- 11 Wireless Hacking
- Speeding Up the Process
- Determining the Target with Airodump-ng
- Cracking WPA/WAP2
- Further Reading
- Attack Scenario
- 12 Web Hacking
- Attacking the Authentication
- Types of Authentication
- Etsy.com Password Reset Vulnerability
- Brute Force Attack
- Further Reading
- Authentication Bypass Using XPATH Injection
- Testing for the Vulnerability
- Authentication Bypass with Insecure Cookie Handling
- How the Attack Works
- Types of SQL Injection
- Testing for SQL Injection
- Guessing Table Names
- Writing Files
- Blind SQL Injection
- Testing for Time-Based SQL Injection
- Reflected/Nonpersistent XSS
- Medium Security
- High Security
- DOM-Based XSS
- Detecting DOM-Based XSS
- Types of DOM-Based XSS
- Demo Pages
- BeEF Modules
- Bypassing CSRF with XSS
- Real-World Example
- Case 1: Blocking Malicious Extensions
- Case 2: Case-Sensitive Bypass
- Real-World Example
- Case 3: When All Dangerous Extensions Are Blocked
- Case 4: Double Extensions Vulnerabilities
- Patching File Inclusions on the Server Side
- Local File Disclosure Vulnerability
- Impact
- Remote SSRF
- Denial of Service
- Full SSRF
- Apache Server
- Reference
- Basic Syntax
- Finding the Username
- Updating the Password
- Symlinking the Configuration File